Freki - Persistent XSS Detector

Freki is a penetration testing tool that enumerates all linked site pages to automate the detection of persistent/stored XSS vulnerabilities for a known (either default or user-crafted) XSS injection.
Getting Started
These instructions will get you a copy of the project up and running on your local machine for development and testing purposes. See deployment for notes on how to deploy the project on a live system.
Prerequisites
If your OS does not have pip installed, use the following command:
sudo easy-install pip
Installing
- Clone the directory
- Enter the directory by typing in this command
cd freki
- Install prerequisite libraries with pip:
pip install -r requirements.txt
- If you are on Linux OS, you can run setup.sh instead:
./setup.sh
This allows Linux OS users to access the program from anywhere on the system using:
freki
Usage
- Run the program with this command:
python freki.py
If you ran setup.sh, you may run the program using this command:
freki
- You will first be prompted to enter the site URL to test for Persistent XSS. An example is:
http://192.168.18.133/dvwa - Enter the payload to be used. An example is:
<script>alert('freki')</script> - If the site requires cookie authentication, provide them in the form:
'keyOne=valueOne;keyTwo=valueTwo' - Finally, indicate if you would like to auto-inject the payload before searching for its presence.
Example Usage:
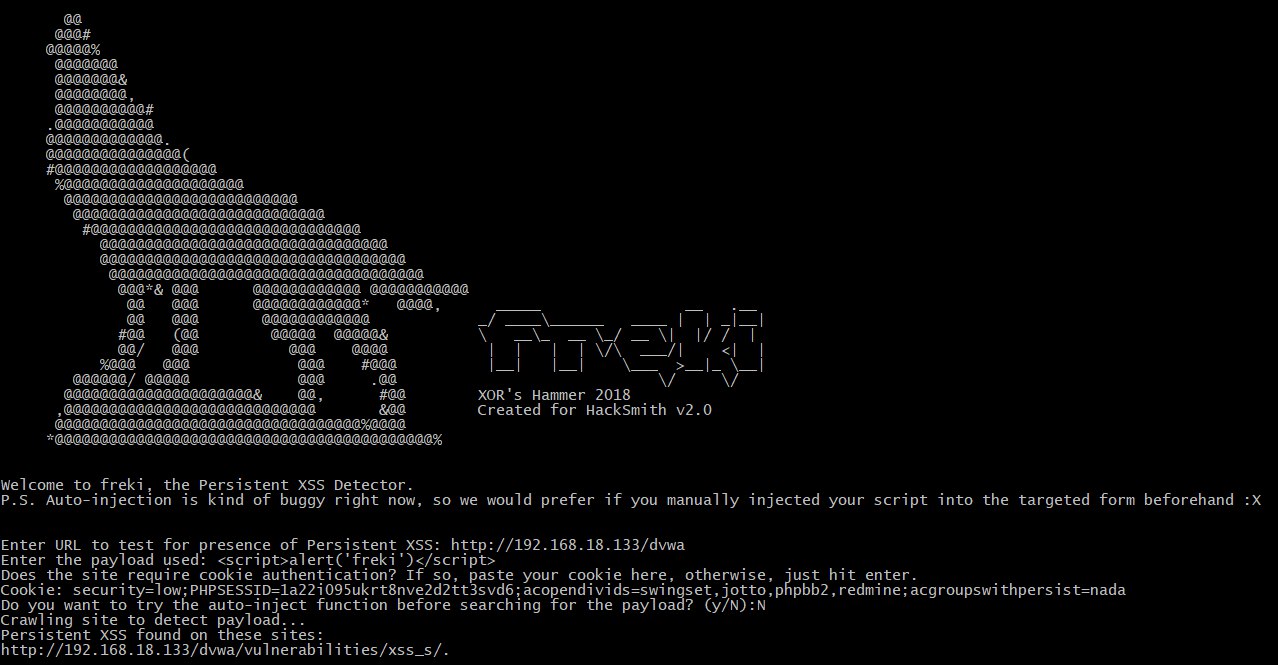
Test Payload found:
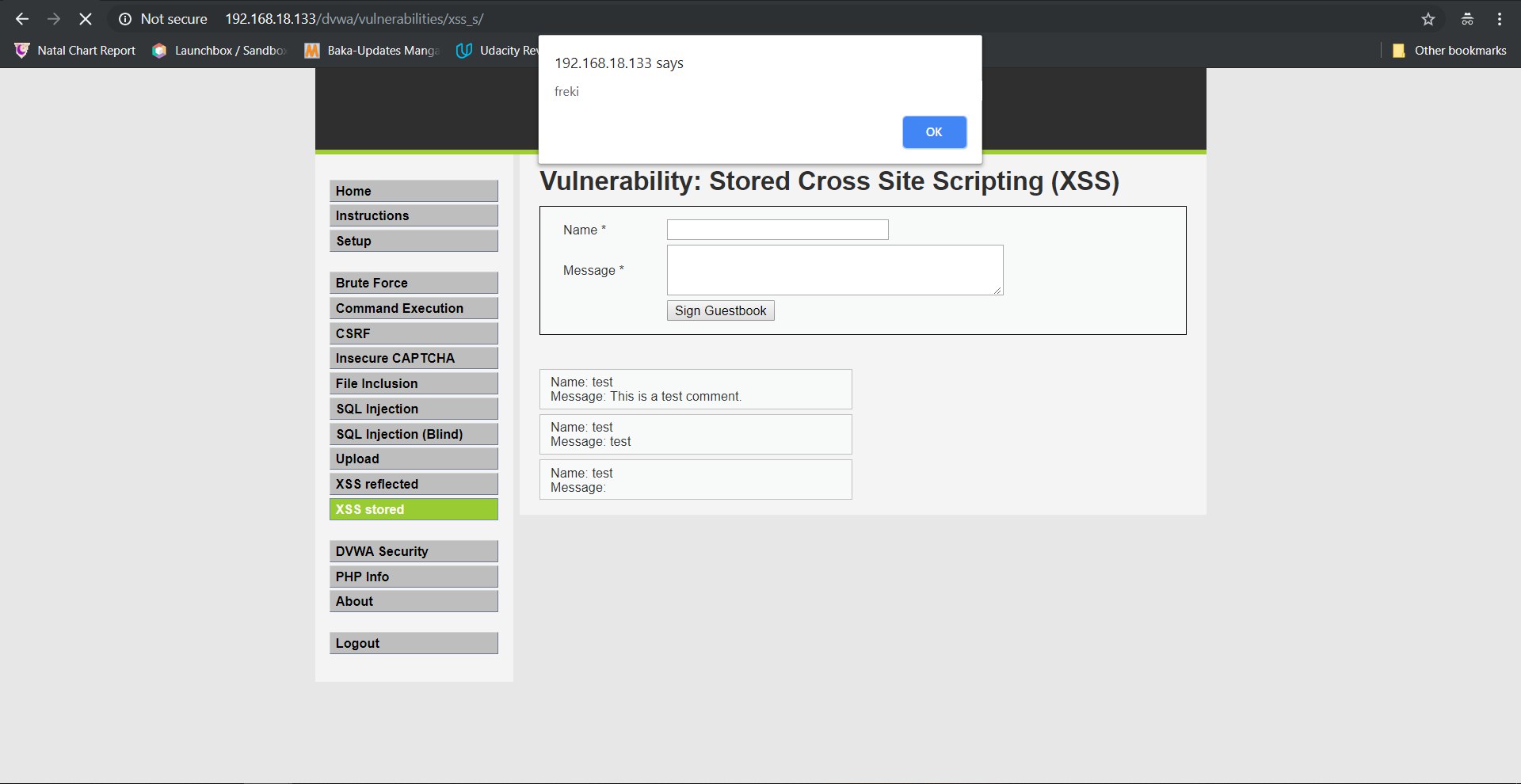
Built With
- Languages
- Python 3.6 - For its standard libraries argparse, contextlib and urllib.
- Frameworks and Libraries
- BeautifulSoup - For dealing with HTML data.
- Requests - To send HTTP requests.
Contributing
Please read our CONTRIBUTING.md for details on our code of conduct, and the process for submitting pull requests to us.
Versioning
For the versions available, see the tags on this repository.
Authors
- Chua Yu Peng - chuayupeng
- Clyde - weizhang05
- Tan Yong He - x3tsunayh
See also the list of contributors who participated in this project.
License
This project is licensed under the GNU GPL v3 - see the LICENSE.md file for details
Acknowledgments
- Hat tip to anyone whose code was used
- Inspiration
- Logo created by Freepik